- Research
- Open access
- Published:
An efficient and secure data sharing scheme for mobile devices in cloud computing
Journal of Cloud Computing volume 9, Article number: 60 (2020)
Abstract
With the development of big data and cloud computing, more and more enterprises prefer to store their data in cloud and share the data among their authorized employees efficiently and securely. So far, many different data sharing schemes in different fields have been proposed. However, sharing sensitive data in cloud still faces some challenges such as achieving data privacy and lightweight operations at resource constrained mobile terminals. Furthermore, most data sharing schemes have no integrity verification mechanism, which would result in wrong computation results for users. To solve the problems, we propose an efficient and secure data sharing scheme for mobile devices in cloud computing. Firstly, the scheme guarantees security and authorized access of shared sensitive data. Secondly, the scheme realizes efficient integrity verification before users share the data to avoid incorrect computation. Finally, the scheme achieves lightweight operations of mobile terminals on both data owner and data requester sides.
Introduction
With the rapid development of information technology and Internet of Things (IoT), enterprises generate more and more big data, which needs to be stored and processed efficiently and securely. Cloud computing is a developed storage platform and has many advantages including low cost and scalability [1,2,3]. Therefore, many enterprises and individuals are apt to outsource their data to cloud for storage and sharing with authorized data requesters. For example, in a cloud based health information system, patients upload their health information to cloud for sharing with medical experts to diagnose diseases. Similarly, the manager of an enterprise not only want to store the big data in cloud, but also want to share the data among their authorized employees wherever needed. Outsourcing data for sharing in cloud not only saves local storage space, but also greatly reduces the cost of enterprises in software purchase and hardware maintenance [4,5,6]. Although people take advantages of this new technology and service, their concerns about data security arises as well. Security problem in cloud is the most critical issue because of the valuable information that data owners share. Cloud providers should address privacy and security issues as a matter of high and urgent priority [7,8,9]. One of the prominent security concerns in data sharing is data privacy. In addition, terminals of users are usually resource-constrained mobile devices with small storage space and low processing speed. Therefore, it is essential to propose an efficient and secure data sharing scheme for mobile devices in cloud computing.
Main contributions
We propose a lightweight and secure sensitive data sharing scheme for mobile devices in cloud computing. The main contributions of the paper are as follows.
-
1)
We design an efficient integrity mechanism based on algebraic signature for sensitive data before data sharing.
-
2)
We guarantee privacy preserving of sensitive data in sharing process and access authorization control for data requesters.
-
3)
We achieve lightweight computation operations on data owner and data requester sides with mobile devices.
Organization
The rest of paper is organized as follows. Section II introduces the related works in secure data sharing. Section III describes architecture and security requirements. Section IV presents the definitions and preliminaries. In section V, we describe the implementations of the efficient data sharing scheme. We analyze security in section VI and evaluate the scheme performance in Section VII. Finally, we conclude this paper in Section VIII.
The related works
With more and more sensitive information sharing among enterprise employees, preserving data integrity and guaranteeing access control for only authorized users to access the data has become the core security problem. Therefore, security problems of data sharing in cloud mainly focus on access control and data integrity [10,11,12,13,14].
At present, data sharing schemes mainly employ access control mechanism to achieve authorized access. Akl and Taylor [15] proposed use of cryptography to realize access control in hierarchical structures. As data owner and the data center are not in the same trusted domain in cloud storage system, access control schemes employing Attributed Based Encryption (ABE) [16] are put forward. ABE commonly comes in Key Policy ABE (KP-ABE) and Cipher text Policy ABE (CP-ABE). KP-ABE uses attributes to describe the encryption data and builds policies into user’s key [17]. CP-ABE uses attributes to describe user’s credentials and the user encrypting the data determines a policy on who can decrypt the data [18]. Lewko [19] proposed the first unbounded KP-ABE scheme. Waters [20] firstly put forward a fully expressed CP-ABE scheme in the standard model. Cheung and Newport [21] proposed another CP-ABE scheme and proved its security in the standard model. To ensure data security in smart health, Zhang and Zhen [22] realize the fine-grained access control, cipher text-policy attribute based encryption (CP-ABE). To achieve privacy and authorized access, many other schemes [23,24,25,26,27,28,29,30,31,32,33] are proposed in diverse fields and applications.
To verify integrity of data in cloud, many integrity verification schemes [26, 34,35,36,37,38,39,40,41,42] have been proposed in recent years. Ateniese [34] proposed the first public auditing scheme, which allows any public verifier to check the data integrity. Later, to prove the integrity of dynamic data, Ateniese [26] proposed another scheme based on the symmetric key provable data possession (PDP) scheme. To support dynamic operation of data, Erway et al. [35] proposed a dynamic provable data possession (DPDP) scheme by introducing an authenticated skip list. Later many auditing schemes are proposed by using the authenticated data structure to support dynamic data update. Zhu et al. [36] introduced an index-hash table (IHT) for dynamic verification. Yang et al. [37] proposed another authenticated data structure called index table (ITable) to store the abstract information of blocks. Tian [38] proposed a data structure named Dynamic-Hash-Table (DHT). Wang et al. [39] and Liu et al. [40] respectively proposed dynamic public auditing schemes based on Merkle Hash Tree (MHT). The two schemes can achieve both public verification and dynamic data operations. However, block signatures are generated by users, which would incur multitude computation and communication overhead on the user side. In 2018, Gan [41] proposed an auditing scheme on algebraic signatures that can achieve lower computation and communication costs. The properties of algebraic signature allows cloud to return a sum of the selected blocks in the proof instead of the original data file, which saves the bandwidth between the cloud and the verifier and make the algebraic signature suited for cloud computing [42]. Nowadays, more and more schemes [23, 43,44,45,46,47,48,49,50,51,52] on cloud computing security are put forward to achieve great advantages.
Architecture and security requirement
System model
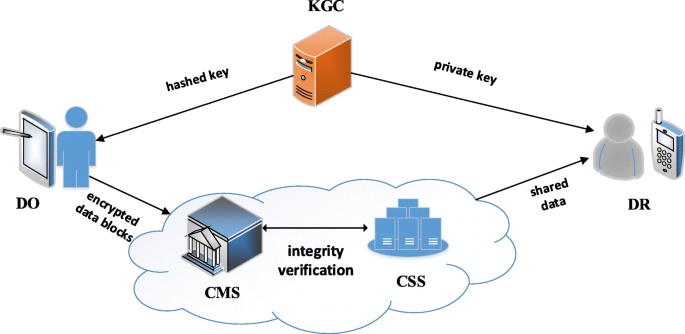
The system model consists of four entities named Key Generator Center (KGC), Data Owner (DO), Cloud Servers (CS) and Data Requester (DR) as depicted in Fig. 1.
Key generation center (KGC)
It is responsible for generating public parameters and master key for the system and issuing private key for other entities.
Data owner (DO)
It is responsible to generate and encrypt the shared data, define access structures, and divide encrypted data into blocks.
Cloud servers (CS)
Cloud servers comes in Cloud Storage Servers (CSS) and Cloud Manage Servers (CMS) based on their roles. CSS is responsible for storing shared data, block tags and supply the data integrity proof. To save computation and communication costs of mobile terminals of DO and DR, CMS is employed to manipulate complex computations including generating algebraic signatures of blocks, verifying data integrity of shared data and computing the intermediate data for encryption and decryption.
Data Requester (DR): It is responsible to download and decrypt the shared data for utilization. In the scheme, only the authorized DR is able to download shared data from CSS and decrypt the data.
In our secure data sharing scheme for mobile terminal devices, DO has large sensitive data to share with legitimate DR. Before sharing, DO encrypts the data with his private key and outsources the data to CSS. If a DR wants to access the data, he must register his identity to KGC and obtain his private key for decryption. To achieve authorized access, only legitimate DRs with correct attributes can download and utilize the shared data. To ensure cloud data intact and decrease computation burden of requesters, CMS helps DR to verify the integrity of data before sharing. Only when data is undamaged, DR downloads and decrypts shared data with his private key.
Security requirement
In the scheme, we suppose CSS and CMS are both semi-trusted. CSS is responsible to store data and block tags for data sharing. However, once data is corrupt or lost, it might launch forge attack or replace attack for economic reasons. Similarly, CMS is curious about the content of sensitive data, so the data should preserve secret to CMS. In the scheme, we assume KGC is a fully trusted authority and can honestly generate private key for the system and other entity. Therefore, the following security requirements of the scheme should be satisfied.
Data confidentiality
The shared data must keep confidential to CSS, CMS and any unauthorized DRs for privacy and security. Any disclosure of shared data is undoubtedly harmful to enterprise benefits. Consequently, it is important to ensure the confidentiality of shared data.
Data integrity
The data should keep intact before shared by DR. It means that the data is undamaged in an unauthorized manner during storage and sharing process.
Authorized access
To achieve authorization, only DR with correct attributes can access shared data stored in CSS.
User revocation
The membership of DR must be revoked to stop his access to shared data when he leaves the organization. To achieve security of the scheme, user revocation should be required in the data sharing scheme.
Design goals
The data sharing scheme for mobile devices is designed to achieve data privacy preservation, data security and lightweight operations.
Privacy preservation
The scheme should satisfy data privacy during data sharing process. As sensitive data is encrypted by data owner before outsourcing to cloud and only authorized data requesters can access the encrypted data, the shared data is private to CSS, CMS and any unauthorized DRs.
Data security
The scheme should achieve sensitive data security during the whole sharing process. The security requirement can be guaranteed by data confidentiality, data integrity, authorized access and user revocation in the scheme.
Lightweight operations
The scheme should decrease computation operations of DO and DR for efficiency. In our scheme, CMS is responsible to divide encrypted data into blocks and computes block tags. Furtherly, when DR wants to access shared data, CMS compute intermediate data of decryption to less DR’s computation burden.
Definitions and preliminaries
Denifitions
-
1)
Discrete Logarithm (DL) Assumption. Suppose g is a generator of multiplicative cyclic group \( \mathbbm{G} \) with prime order q. On input \( \boldsymbol{y}\mathbf{\in}\mathbbm{G} \), there does not exist probabilistic polynomial time algorithm that outputs a value \( \boldsymbol{x}\boldsymbol{\in }{\boldsymbol{Z}}_{\boldsymbol{q}}^{\ast} \) such that gx = y with non-negligible probability.
-
2)
Computational Diffie-Hellman (CDH) Assumption. Suppose g is a generator of multiplicative cyclic group \( \mathbbm{G} \) with prime order q. On input \( {\boldsymbol{g}}^{\boldsymbol{x}},{\boldsymbol{g}}^{\boldsymbol{y}}\mathbf{\in}\mathbbm{G} \), there does not exist probabilistic polynomial time algorithm that outputs \( {\boldsymbol{g}}^{\boldsymbol{xy}}\mathbf{\in}\mathbbm{G} \) with non-negligible probability.
-
3)
Access Structure. Suppose P = {P1, P2, …, Pn} is a set of parties. A collection of W ⊆ 2P is monotone if ∀B,C : B ∈ W and B ⊆ C then C ∈ W. An access structure is the collection W with non-empty subsets of P, i.e., W ⊆ 2P\{∅}. The sets in W are named as authorized sets, and the sets not in W are named as the unauthorized sets.
Preliminaries
-
1.
Linear secret-sharing schemes (LSSS). LSSS is a share-generating matrix A with rows labeled by attributes. Assume S ∈ A is an authorized set and I is defined as I = {i| ρ(i) ∈ S}. Then there exists constants ωi ∈ Zq satisfying ∑i ∈ Iωiλi = s where λi is valid share of secret share s. suppose Ai is the ith row of A, the equation ∑i ∈ IωiAi = (1, 0, …, 0) also satisfies.
-
2.
Algebraic signature. The algebraic signature of a file block composed of strings s0,s1,…,sn − 1 is defined as \( {\boldsymbol{s}\boldsymbol{ig}}_{\boldsymbol{g}}\left({\boldsymbol{s}}_{\mathbf{0}},{\boldsymbol{s}}_{\mathbf{1},}\dots, {\boldsymbol{s}}_{\boldsymbol{n}-\mathbf{1}}\right)={\sum}_{\boldsymbol{i}=\mathbf{0}}^{\boldsymbol{n}-\mathbf{1}}{\boldsymbol{s}}_{\boldsymbol{i}}\cdotp {\boldsymbol{g}}^{\boldsymbol{i}} \) . The algebraic signature has the following two properties: i) the algebraic signature of a combination of file F1 and file F2 is defined as sigg(F1 ⨁ F2) = sigg(F1) ⨁ sigg(F2) . Ii) the algebraic signature of a combination of n blocks in file F is equal to the combination of algebraic signatures of each block named \( {\boldsymbol{m}}_{\boldsymbol{i}}\in \mathbbm{G} \), which is described as \( {\sum}_{\boldsymbol{i}=\mathbf{1}}^{\boldsymbol{n}}{\boldsymbol{sig}}_{\boldsymbol{g}}\left({\boldsymbol{m}}_{\boldsymbol{i}}\right)={\boldsymbol{sig}}_{\boldsymbol{g}}{\sum}_{\boldsymbol{i}=\mathbf{1}}^{\boldsymbol{n}}{\boldsymbol{m}}_{\boldsymbol{i}} \).
-
3.
XOR-homomorphic function. A XOR-homomorphic function h is a pseudo-random function that can ensure data privacy. Its properties is as follows. For any inputs x,y, there exists h(x ⨁ y) = h(x) ⨁ h(y).
-
4.
Bilinear maps. Suppose \( {\mathbbm{G}}_{\mathbf{1}},{\mathbbm{G}}_{\mathbf{2}} \) are two multiplicative groups with same large prime order q, and g is a generator of \( {\mathbbm{G}}_{\mathbf{1}} \). A bilinear map e is a map function \( \boldsymbol{e}:{\mathbbm{G}}_{\mathbf{1}}\times {\mathbbm{G}}_{\mathbf{2}}\boldsymbol{\to}{\mathbbm{G}}_{\mathbf{1}} \) with the following properties: i) computability. \( \boldsymbol{\forall}\boldsymbol{u},\boldsymbol{v}\boldsymbol{\in }{\mathbbm{G}}_{\mathbf{1}} \), an efficient algorithm exists to compute e(u, v). Ii) Binearity. ∀a,b ∈ Zq, ∃ e(ua, vb) = e(u, v)ab. Iii) nondegeneracy. e[g, g] ≠ 1. Iv) security. It is hard to compute discrete logarithm (DL) in \( {\mathbbm{G}}_{\mathbf{1}} \).
Notations
Table 1 describes the main notations in the scheme.
Scheme implementations
In this section, we present the efficient and secure data sharing scheme for mobile devices in cloud computing in detail. We divide the sharing scheme into four phases named initial phase, data processing phase, integrity verification phase and data sharing phase.
Initial phase
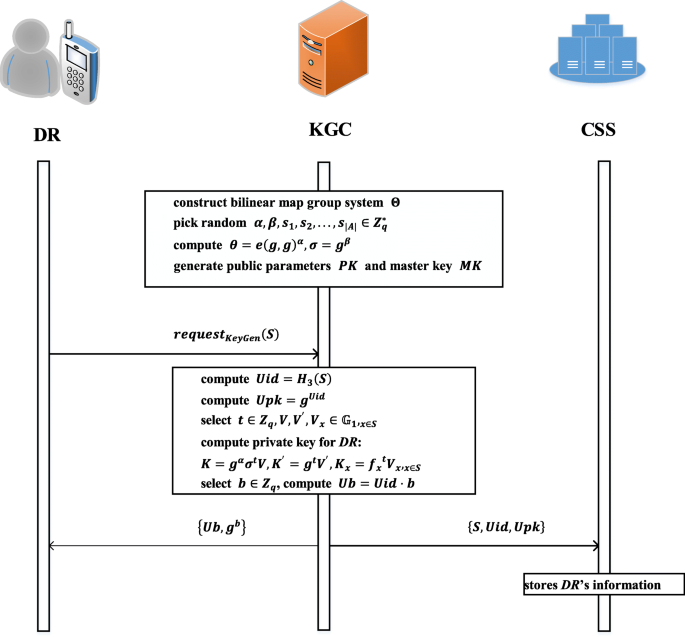
This phase consists of three algorithms named ParaSetup,KeyGen,IdReg. Algorithm ParaSetup is mainly responsible to generate system parameters before data sharing. Algorithm KeyGen is mainly used to obtain the private key for DR to decrypt the cipher-text of shared data. Algorithm IdReg is responsible for registering DR’s identity information in a table for checking the validity of DR. Figure 2 describes the data flow of the phase.
-
1)
ParaSetup( λ, A) → (PK, MK):It is run by KGC. Given system security parameter λ, KGC constructs the bilinear map group system \( \Theta =\left({\mathbbm{G}}_1,{\mathbbm{G}}_2,q,e\right) \) where \( {\mathbbm{G}}_1,{\mathbbm{G}}_2 \) are multiplicative groups with prime order q, and e is a bilinear map \( e:{\mathbbm{G}}_1\times {\mathbbm{G}}_1\to {\mathbbm{G}}_2 \). Suppose A is the attribute universe A whose attribute number is ∣A∣. KGC picks random \( \alpha, \beta, {s}_1,{s}_2,\dots, {s}_{\mid A\mid}\in {Z}_q^{\ast } \) and computes θ = e(g, g)α, σ = gβ. Then KGC defines heteromorphic function h \( :{\mathbbm{G}}_1\to {\mathbbm{G}}_1 \) and algebraic signature sigg(mi) = mi · gi, where \( {m}_i\in {\mathbbm{G}}_1 \) and g is a generator of \( {\mathbbm{G}}_1 \). Next, KGC selects three secure hash function \( {H}_1:{\left\{0,1\right\}}^{\ast}\to {\mathbbm{G}}_1,{H}_2:{\mathbbm{G}}_1\to {\left\{0,1\right\}}^{len},{H}_3:{\left\{0,1\right\}}^{\ast}\to {Z}_q^{\ast } \). KGC publishes public parameters \( PK=\left(e,g,{H}_1,{H}_2,{H}_3,h,{sig}_g,\theta, \sigma, {f}_i={g}^{s_i}{,}_{1\le i\le \left|A\right|}\right) \) and keeps master key MK = (α, β) secretly.
-
2)
KeyGen(MK, S) → (Usk): It is run by KGC. Before DR with attribute S share the data, he should get the private key to decrypt the cipher text of shared data. DR first sends key generation request requestKeyGen(S) to KGC. After receiving the request, KGC computes Uid = H3(S) as the DR identity and computes Upk = gUid as DR’s public key. Next KGC selects \( \boldsymbol{t}\boldsymbol{\in }{\boldsymbol{Z}}_{\boldsymbol{q}},\boldsymbol{V},{\boldsymbol{V}}^{\prime },{\boldsymbol{V}}_{\boldsymbol{x}}\boldsymbol{\in}{\mathbbm{G}}_{\mathbf{1}}{,}_{\boldsymbol{x}\boldsymbol{\in}\boldsymbol{S}} \) and computes the private key Usk for DR as follows: K = gασtV,K′ = gtV′,Kx = fxtVx,x ∈ S. KGC randomly selects b ∈ Zq and computes Ub = Uid · b and sends {Ub, gb} to CMS for later integrity verification . Then, KGC sends {Uid, Usk} to DR and {S, Uid, Upk} to CSS.
-
3)
IdReg(S, Uid) → DRTable. It is run by CSS. To verify the validity of DR before transferring the shared data, CSS stores DR’s information including identity Uid, attribute set S and public key Upk in a table named DRTable. If identity of DR is valid, CSS transfers shared data to him. Otherwise, CSS refuses the download request of DR.
Data processing phase
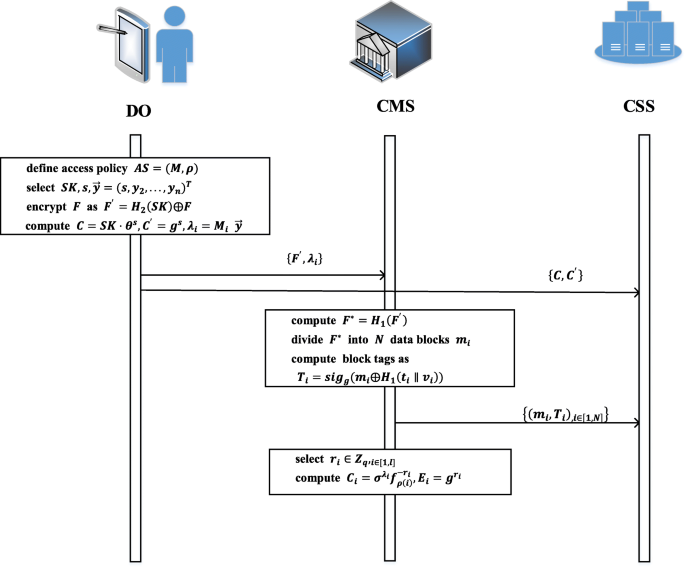
The phase includes two algorithms named DataEnc, TagGen and InterEnc. To achieve confidentiality, algorithm DataEnc encrypts shared data and divides the data into blocks. To ensure the data is intact, algorithm TagGen generates block tag for each block. To decrease DO’s computation burden, algorithm InterEnc helps DO computer the intermediate value for encryption. Fig. 3 describes the data flow of the phase.
-
1)
DataEnc( F) → (F′): It is run by DO. To ensure only authorized DR have access to shared data, DO adefines access policy AS = (M, ρ), where M is a l × n matrix and ρ is the function that maps each row of the matrix to an associated attribute. That is, for i ∈ [1, l], the value ρ(i) is the attribute associated with row i. Suppose the shared data is F ∈ {0, 1}len, where len is the max length of F and the identity is Fid. DO selects key \( SK\in {\mathbbm{G}}_1,s\in {Z}_q \) and a random column vector \( \overrightarrow{y}={\left(s,{y}_2,\dots, {y}_n\right)}^T\in {Z}_q^n \). Next, he encrypts F as F′ = H2(SK) ⨁ F and computes \( C= SK\cdotp {\theta}^s,{C}^{\prime }={g}^s,{\lambda}_i={M}_i\ {\overrightarrow{y,}}_{1\le i\le l} \). Finally, DO sends {F′, λi} to CMS and {C, C′} sends to CSS.
-
2)
TagGen( F′) → (Ti): It is run by CMS. CMS computes F∗ = H1(F′) and divides F∗ into N data blocks named mi. Suppose ti, vi represent the recent timestamp and version of each block mi. CMS computes block tags as follows
and sends {(mi, Ti),i ∈ [1, N]} to CSS.
-
3)
InterEnc( M) → (Ci, Ei). It is run by CMS. To decrease the computation burden of mobile devices at DO side, CMS helps to compute the intermediate encryption data. He selects ri ∈ Zq,i ∈ [1, l] and computes \( {C}_i={\sigma}^{\lambda_i}{f}_{\rho (i)}^{-{r}_i},{E}_i={g}^{r_i} \). For later integrity verification, CMS stores the intermediate data Ci, , Ei locally.
Integrity verification phase
When DR wants to access shared data, he first sends integrity request to CMS for verifying whether the data is intact. Then CMS generates integrity challenge ch and sends it to CSS. After getting the challenge, CSS computes data proof P and sends it to CMS to verify the integrity. This phase consists of the following three algorithms and Fig. 4 describes the data flow of the phase.
-
1)
ChalGen( Fid) → (ch): Before downloading shared data, DR first sends request requestchallen(Fid, Uid) to CMS for integrity verification. After receiving the request, CMS verifies the validity of DR’s identity with equation e(Upk, gb) = e(g, g)Ub. If the equation does not hold, CMS rejects the request. Otherwise, CMS randomly selects c blocks and corresponding random numbers \( {R}_i\in {Z}_q^{\ast } \). Then CMS sends challenge ch = (i, Ri),i ∈ [1, c] to CSS.
-
2)
ProfGen( Ti, F′) → (P): After receiving ch from CMS, CSS computes data proof and tag proof
Then he sends proof P = (DP, TP) to CMS.
-
3)
IntegityVer( P) → (true, false).After getting the proof P , CMS computes \( L={\sum}_{i=1}^c{sig}_g\left(h\left({R}_i\right)\oplus {H}_1\left({t}_i\parallel {v}_i\right)\right) \) and verifies whether the following equation holds.
If the equation holds, it indicates that the data is intact and outputs true, Otherwise, CMS outputs false.
Data sharing phase
If the shared data is intact, DR downloads and decrypts F′. This phase consists of the following four algorithms and Fig. 5 describes the data flow of the phase.
-
1)
InvalidyCheck( S, Uid) → (true, false). It is run by CSS. Before downloading shared data F′, DR sends request requestdownload(Fid, S, Uid) to CSS. Then CSS scans DRTable to verify whether DR is legitimate. If DR is in DRTable, CSS transfers {C, F′} to DR. Otherwise, CSS refuses the request.
-
2)
InterDec( Ci, Ei, K′, Kρ(i)) → (W). If the shared data is intact, CMS computes the intermediate value for DR to decrease the computation burden of DR side. Let ={i : ρ(i) ∈ S} ⊆ [1, l] , where S is the attribute of DR. Suppose ωi ∈ Zq,i ∈ I is constant and satisfies the equation ∑i ∈ IωiAi = (1, 0, …, 0). CMS computes \( W={\prod}_{i\in I}{\left(e\left({C}_i,{K}^{\prime}\right)e\left({E}_i,{K}_{\rho (i)}\right)\right)}^{\omega_i} \) and sends W to DR securely.
-
3)
Decryption( F′) → (F): If DR is legitimate, he downloads F′ and computes the follows.
Then DR computes SK = C/CK′, F = H2(SK) ⨁ F′ and recovers the plaintext of shared data .
-
4)
Revocation( Uid) → (DRTable). DR can be revoked after leaving the organization. After revocation of DR, DSS deletes DR’s information from DRTable and DR cannot download the shared file later.
Security analysis
In this section, we analyze the security of the scheme, including correctness, unforgeability and privacy.
Theorem 1. Authorized DR can correctly verify the integrity of the data stored in CSS.
Proof. Theorem 1 can be proved by verifying the correctness of eq. (4). The proof is as follows.
From the proof of eq. (4), DR can verify whether the data is undamaged stored in CSS.
Theorem 2. Authorized DR can correctly recover the shared data if he owns the legal attributes.
Proof. Theorem 2 can be proved by verifying the correctness of eq. (5). The proof is as follows.
Then DR computes SK = C/CK′,F = H2(SK) ⨁ F′ to recover the plaintext of shared data.
Theorem 3. It is computationally infeasible for CSS, CMS and unauthorized DR to get the plaintext of health data in the scheme.
Proof. In data processing phase, DO encrypts file F to F′ with F′ = H2(SK) ⨁ F, where SK is only secret to DO. Therefore, the file is confidential to both CSS and CMS. The confidentiality guarantee depends on the security of hash function H2. As H2 is a secure one-way hash function, the data is private to CSS and CMS. In data sharing phase, CSS sends { C, F′} to DR, where C = SK · θs and F′ is the cipher text of shared data. CMS computes the intermediate value for DR to decrypt the shared data F′ only if DR’s attributes satisfy the access structure. Therefore, any unauthorized DR cannot get any information on the sensitive data.
Theorem 4. It is computationally impossible for CSS to forge an integrity proof to pass the public verification, if XOR-homomorphic function is secure.
Proof. We can prove the theorem with the following games. In the games, we suppose the adversary is the party who forge an integrity proof to pass the public verification.
Game 1 is the challenge game. The challenger generates public-private key pair ( PK, MK) and provides PK to the adversary. The adversary is able to interact with the challenger and query some data blocks. Then the challenger computes corresponding block tags and returns the tags to the adversary. When challenger launches challenge to the adversary, he can respond to the challenger with data proof and tag proof.
Game 2 is another challenge game in which the challenger keeps all the tags ever issued as part of the queries. If the challenger detects the aggregated block tags TP is not equal to \( TP={\sum}_{i=1}^c{T}_i \), he declares the game fails.
Game 3 is the same as game 2 with one difference that the challenger keeps all response sequences to the adversary’s queries. Suppose the challenger sends ch = (i, Ri) to the adversary, the adversary’s reply to the query is P = (DP, TP) where \( T={\sum}_{i=1}^c{T}_i \). In the scheme, P is the correct proof and equation DP = TP ⨁ L holds. Suppose the adversary’s proof is P′ = (DP′, TP′), where \( {TP}^{\prime }={\sum}_{i=1}^c{T_i}^{\prime } \), then the equation DP′ = TP′ ⨁ L also holds. We define △DP = DP′ ⨁ DP, △TP = TP′ ⨁ TP.We make the XOR operation on the above two verification equations and get △DP = △ DP. The above equation holds with the probability is \( \frac{1}{q} \). The probability can be negligible.
Performance evaluation
In this section, we evaluate the computation costs of DO and DR in the scheme and compare it with scheme [22].
Performance analysis of mobile terminals
To analyze computation overhead of the scheme, we define the following notations to denote the corresponding operations: Let Pair denote a paring operation, Hash denote a hash operation and Exp denote an exponentiation operation. Similarly, Mul represents a multiplication operation. Xor and Sig respectively denote XOR and algebraic signature operation of the scheme.
-
1)
Computation overhead of DO side
The computation overhead of DO is mainly in encryption phase. DO first computes \( {\boldsymbol{F}}^{\prime }={\boldsymbol{H}}_{\mathbf{2}}\left(\boldsymbol{K}\right)\boldsymbol{\bigoplus}\boldsymbol{F},\boldsymbol{C}=\boldsymbol{K}\cdotp {\boldsymbol{\theta}}^{\boldsymbol{s}},{\boldsymbol{C}}^{\prime }={\boldsymbol{g}}^{\boldsymbol{s}},{\boldsymbol{\lambda}}_{\boldsymbol{i}}={\boldsymbol{M}}_{\boldsymbol{i}}\ {\overrightarrow{\boldsymbol{y}}}_{,\mathbf{1}\boldsymbol{\le}\boldsymbol{i}\boldsymbol{\le}\boldsymbol{l}} \). Therefore, the computation overhead of DO side is (1 + l)Mul + 2Exp + Hash + Xor.
-
2)
Computation overhead of DR side
The computation overhead of DR is mainly in data sharing phase. DR downloads F′ and computes \( {\boldsymbol{C}\boldsymbol{K}}^{\prime }=\frac{\boldsymbol{e}\left({\boldsymbol{C}}^{\prime },\boldsymbol{K}\right)}{\mathbf{V}}={\boldsymbol{\theta}}^{\boldsymbol{s}} \). Then DR gets K = C/CK′ and recovers the plaintext F = H2(K) ⨁ F′. Therefore, the computation overhead of DR side is Pair + Xor + 2Div.
Table. 2 illustrates the computation overhead of mobile terminals on both sides.
Experimental results
We simulate our scheme with the Pairing Based Cryptography (PBC) library of version 0.5.14. We compare the computation time of DO and DU with scheme [22] by utilizing an MNT d159 curve with 160-bit group order. All the experiment results represent the average of 20 trials.
-
1)
Computation time of DO in processing phase
The computation time of DO mainly generates in algorithm DataEnc of data processing phase. We first test the relation between DO’s computation time and the size of attribute universe A as described in Fig. 6. We can see that when size of attribute universe A varies from 1 to 100, the computation time of DO increases slowly and costs less time than Zhang’s. Then we test the relation between DO’s computation time and the size of shared data as described in Fig. 7. From Fig. 7, we can conclude that DO’s computation time in our scheme is lower than that of Zhang’s scheme when shared data varies from 1 M to 10 M.
-
2)
Computation time of DR in data sharing phase
In data sharing phase, we first test the relationship between DR’s computation time and the size of attribute universe A as described in Fig. 8. Because CMS help DR to computes the intermediate data of decryption, DR’s computation time is constant when the size of attribute universe A increases. We also test the relationship between DR’s computation time and the size of shared data as described in Fig. 9. We can see that with the size of shared data growing, the computation time of DR increases slowly. From Figs. 8 and 9, we can conclude that DR’s computation time in our scheme is less than that in Zhang’s scheme.
Conclusion
In this paper, we propose an efficient and secure data sharing scheme for mobile devices. The scheme guarantees security and authorized access of shared sensitive data. Furtherly, the scheme realizes efficient integrity verification before DR shares the data to avoid incorrect computation. Finally, the scheme achieves lightweight operations of mobile terminals on both DO and DR sides.
Availability of data and materials
The data used to support the findings of this study is available from the corresponding author upon request.
Abbreviations
- KGC:
-
Key Generator Center
- DO:
-
Data Owner
- CS:
-
Cloud Servers
- DR:
-
Data Requester
- CSP:
-
Cloud Storage Servers
- CMS:
-
Cloud Manage Servers
- KP-ABE:
-
Key Policy Attribute Based Encryption
- CP-ABE:
-
Cipher Text Policy Attribute Based Encryption
References
Farahat IS, Tolba AS (2018) A secure real-time internet of medical smart things (IOMST). Comput Electrical Eng 72:455–467
Rahmani AM, Gia TN, Negash KB (2018) Exploiting smart e-Health gateways at the edge of healthcare Internet-of-Things: A fog computing approach. Futur Gener Comput Syst 78:641–658
Zhang Y, Qiu M, Tsai C, Hassan M, Alamri A (2017) Health-CPS: healthcare cyber-physical system assisted by cloud and big data. IEEE Syst J 11:88–95
Ghazvini A, Shukur Z (2013) Security challenges and success factors of electronic healthcare system. Proc Technol 11:212–219
Guan Z, Lv Z, Du X et al (2019) Achieving data utility-privacy tradeoff in internet of medical things: a machine learning approach. Futur Gener Comput Syst 98:60–68
Elhoseny M, Abdelaziz A (2018) A hybrid model of internet of things and cloud computing to manage big data in health services applications. Futur Gener Comput Syst 86:1383–1394
Han K, Li Q, Deng Z (2016) Security and efficiency data sharing scheme for cloud storage. Chaos Solitons Fractals 86:107–116
Zhang L, Zhang H, Jia Y (2020) Blockchain-based two-party fair contract signing scheme. Inf Sci 535:142–155
Lu X, Cheng X (2020) A secure and lightweight data sharing scheme for internet of medical things. IEEE Access 8:5022–5030. https://doi.org/10.1109/ACCESS.2019.2962729
Bahga A, Madisetti VK (2013) A cloud-based approach for interoperable electronic health records (EHRs). IEEE J Biomed Health Inf 17(5):894–906
Tawalbeh LA, Mehmood R, Benkhlifa E, Song H (2016) Mobile cloud computing model and big data analysis for healthcare applications. IEEE Access 4:6171–6180
Nguyen DC, Pathirana PN, Ding M, Seneviratne A (2019) Blockchain for Secure EHRs Sharing of Mobile Cloud Based E-Health Systems. IEEE Access 7:66792–66806. https://doi.org/10.1109/ACCESS.2019.2917555
Chang V (2017) Towards data analysis for weather cloud computing. Knowl Based Syst 127:29–45
Gao F, Sunyaev A et al (2019) Context matters: a review of the determinant factors in the decision to adopt cloud computing in healthcare. Int J Inf Manag 48:120–138
Akl SG, Taylor PD (1983) Cryptographic solution to a problem of access control in a hierarchy. ACM Trans Comput Syst 1:239–248
Goyal V, Pandy O, Sahai A, Waters B (2006) Attribute-based encryption for fine-grained access control of encrypted data. In: Proceedings of the 13th ACM conference on Computer and communications security, p 89
Hur J, Noh CD (2011) Attribute-based access control with efficient revocation in data outsourcing systems. IEEE Trans Parallel Distributed Syst 22:1214–1221
Bethencourt J, Sahai A, Waters B (2007) Ciphertext-policy attribute based encryption. In: Proceedings of the IEEE symposium on security privacy, p 321
Lewko A, Waters B (2011) Decentralizing attribute-based encryption. In: Proceedings of the 30th Annual international conference on Theory and applications of cryptographic techniques: advances in cryptolog, p 568
Waters B (2011) Ciphertext-policy attribute-based encryption: an expressive, efficient, and provably secure realization. In: Proceedings of the International Workshop on Public Key Cryptography, pp 53–70
Cheung L, Newport C (2007) Provably secure ciphertext policy ABE. In: Proc. ACM Conf. Comput. Commun. Security (CCS), pp 456–465
Zhang Y, Zhen D, Deng R (2018) Security and privacy in smart health: efficient policy-hiding attribute-based access control. IEEE Internet Things J 5:2130–2145
Yang M, Zhang T (2018) Efficient Privacy-Preserving Access Control Scheme in Electronic Health Records System. Sensors 18:3520–3545.
Phuong T, Yang G, Susilo W (2016) Hidden ciphertext policy attribute-based encryption under standard assumptions. IEEE Trans Inf Forensic Secur 11:35–45
Zhang Y, Chen F, Li J (2017) Ensuring attribute privacy protection and fast decryption for outsourced data security in mobile cloud computing. Inf Sci 379:42–61
Ateniese G, PietroR D, Mancini LV, Tsudik G (2008) Scalable and efficient provable data possession. In: Proceedings of the 4th international conference on Security and privacy in communication networks, pp 1–10
Yang K (2017) An efficient and fine-grained big data access control scheme with privacy-preserving policy. IEEE Internet Things Journal 4:563–571
Wang G, Liu Q, Wu J Hierarchical attribute-based encryption and scalable user revocation for sharing data in cloud servers. Comput Secur 30:320–331
Guo Z, Li M, Fan X (2013) Attribute-based ring signcryption scheme. Secur Commun Netw 6:790–796
Wei J, Hu X, Liu W (2014) Traceable attribute-based signcryption. Secur Commun Netw 7:2302–2317
Liu J, Huang X, Liu JK (2015) Secure sharing of personal health records in cloud computing: Ciphertext-policy attribute-based signcryption. Futur Gener Comput Syst 52:67–76
Hu C, Li W (2017) A secure and verifiable access control scheme for big data storage in clouds. IEEE Trans Big Data 4:341–355
Cai H, Xu B, Jiang L (2017) IoT-based big data storage systems in cloud computing: perspectives and challenges. IEEE Internet Things 4:75–87
Ateniese G, Burns R, Curtmola R (2007) Provable data possession at untrusted stores. ACM Conf Comput Commun Secur 14:598–609
Erway C, Papamanthou C, Tamassia R (2009) Dynamic provable data possession. ACM Conf Comput Commun Secur 17:213–222
Zhu Y, Ahn GJ, Hu H, Yau SS (2013) Dynamic audit services for outsourced storages in clouds. IEEE Trans Serv Comput 6:227–238
Yang K, Jia X (2013) An efficient and secure dynamic auditing protocol for data storage in cloud computing. IEEE Trans Parallel Distributed Syst 24:1717–1726
Tian H, Chen Y, Chang CC (2017) Dynamic-hash-table based public auditing for secure cloud storage. IEEE Trans Serv Comput 10:701–714
Wang Q, Wang C, Ren K, Lou W (2011) Enabling public auditability and data dynamics for storage security in cloud computing. IEEE Trans Parallel Distributed Syst 22:847–859
Liu C, Chen J, Yang LT, Zhang X (2014) Authorized public auditing of dynamic big data storage on cloud with efficient verifiable fine-grained updates. IEEE Trans Parallel Distributed Syst 25:2234–2244
Gan Q, Wang X, Fang X (2018) Efficient and secure auditing scheme for outsourced big data with dynamicity in cloud. Inf Sci 61:93–107
Luo Y, Fu S, Xu M (2014) Enable data dynamics for algebraic signatures based remote data possession checking in the cloud storage. China Commun 11:114–124
Bhaskaran K, Ilfrich P, Liffman D (2018) Double-blind consent-driven data sharing on blockchain. In: Cloud Engineering (IC2E), IEEE International Conference on IEEE, pp 385–439
Liu CW, Hsien WF, Yang CC (2016) A survey of public auditing for shared data storage with DU revocation in cloud computing. Int J Netw Secur 18:650–666
Shamir A (1985) Identity-Based Cryptosystems and Signature Schemes. In: Blakley GR, Chaum D (eds) Advances in Cryptology. CRYPTO 1984. Lecture Notes in Computer Science, vol 196. Springer, Berlin, Heidelberg. https://doi.org/10.1007/3-540-39568-7_5
Yoon E-J, Choi Y, Kim C (2013) New ID-based proxy signature scheme with message recovery. In: Grid and Pervasive Computing (Lecture Notes in Computer Science), vol 7861. Springer-Verlag, Berlin, pp 945–951
Yu J, Hao R (2019) Comments on SEPDP: secure and efficient privacy preserving provable data possession in cloud storage. IEEE Trans Serv Comput. https://doi.org/10.1109/TSC.2019.2912379
Lu XQ, Pan ZK, Xian HQ (2020) An integrity verification scheme of cloud storage for internet-of-things mobile terminal devices. Comput Secur 92. https://doi.org/10.1016/j.cose.2019.101686
Y. Zhang, J. Yu, R. Hao, C, Wang, K. Ren, “Enabling Efficient User Revocation in Identity-based Cloud Storage Auditing for Shared Big Data,” IEEE Trans Dependable Secure Comput, vol. 17, pp. 608–619, 2020
Shen W, Su Y, Hao R (2020) Lightweight cloud storage auditing with Deduplication supporting strong privacy protection. IEEE Access 8:44359–44372
Zhao P, Yu J, Zhang H (2020) How to securely outsource finding the min-cut of undirected edge-weighted graphs. IEEE Trans Inf Forensic Secur 15:315–328
Zhang H, Jia Y, Cheng L (2020) Practical and secure outsourcing algorithms for solving quadratic congruences in internet of things. IEEE Internet Things J 7:2968–2981
Acknowledgments
We sincerely thank the Reviewers and the Editor for their valuable suggestions.
Funding
This work is supported in part by Natural Science Foundation of China under Grant No. 61772294 and Grant No. 61602214, in part by Natural Science Foundation of Shandong Province under Grant No. ZR2019LZH002.
Author information
Authors and Affiliations
Contributions
Xiuqing Lu, Zhenkuan Pan, Hequn Xian designed the study and write the paper. Hequn Xian performed the simulations. Xiuqing Lu, Zhenkuan Pan wrote the paper. All authors reviewed and edited the manuscript. All authors read and approved the final manuscript.
Corresponding author
Ethics declarations
Competing interests
The authors declare that they have no competing interests.
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Lu, X., Pan, Z. & Xian, H. An efficient and secure data sharing scheme for mobile devices in cloud computing. J Cloud Comp 9, 60 (2020). https://doi.org/10.1186/s13677-020-00207-5
Received:
Accepted:
Published:
DOI: https://doi.org/10.1186/s13677-020-00207-5